
Heading
Lorem ipsum dolor sit amet, consectetur adipiscing elit. Suspendisse varius enim in eros elementum tristique. Duis cursus, mi quis viverra ornare, eros dolor interdum nulla, ut commodo diam libero vitae erat. Aenean faucibus nibh et justo cursus id rutrum lorem imperdiet. Nunc ut sem vitae risus tristique posuere.
Last updated on
October 15, 2025
min read
As cyber threats become more sophisticated, protecting your business from data breaches and cyberattacks have never been more critical. Vulnerability Assessment and Penetration Testing (VAPT) is a crucial component of a comprehensive cybersecurity plan for businesses of all sizes. Just like how regular health checkups help us maintain our physical well-being, VAPT helps businesses assess their cybersecurity posture, identify vulnerabilities, and take the necessary steps to address them before attackers can exploit them.
The need for VAPT: Data Breaches & Emerging Threats
The statistics on data breaches and leaks are alarming, nearly 94 million records worldwide were exposed and the average cost of a breach globally rose to USD 4.44 million, in just the first half of 2025. The COVID-19 pandemic has created new opportunities for cybercriminals, just like how a change in lifestyle can affect our health. The surge in remote work and online activity has made businesses more vulnerable to cyber threats.
The table provided displays a list of prominent data breaches that have occurred in recent years, highlighting the importance of having a strong cybersecurity plan in place, as such incidents can occur in every industry.

The Forrester indicates that cybercrime expected to cost $12 trillion in 2025, despite efforts to improve cybersecurity.
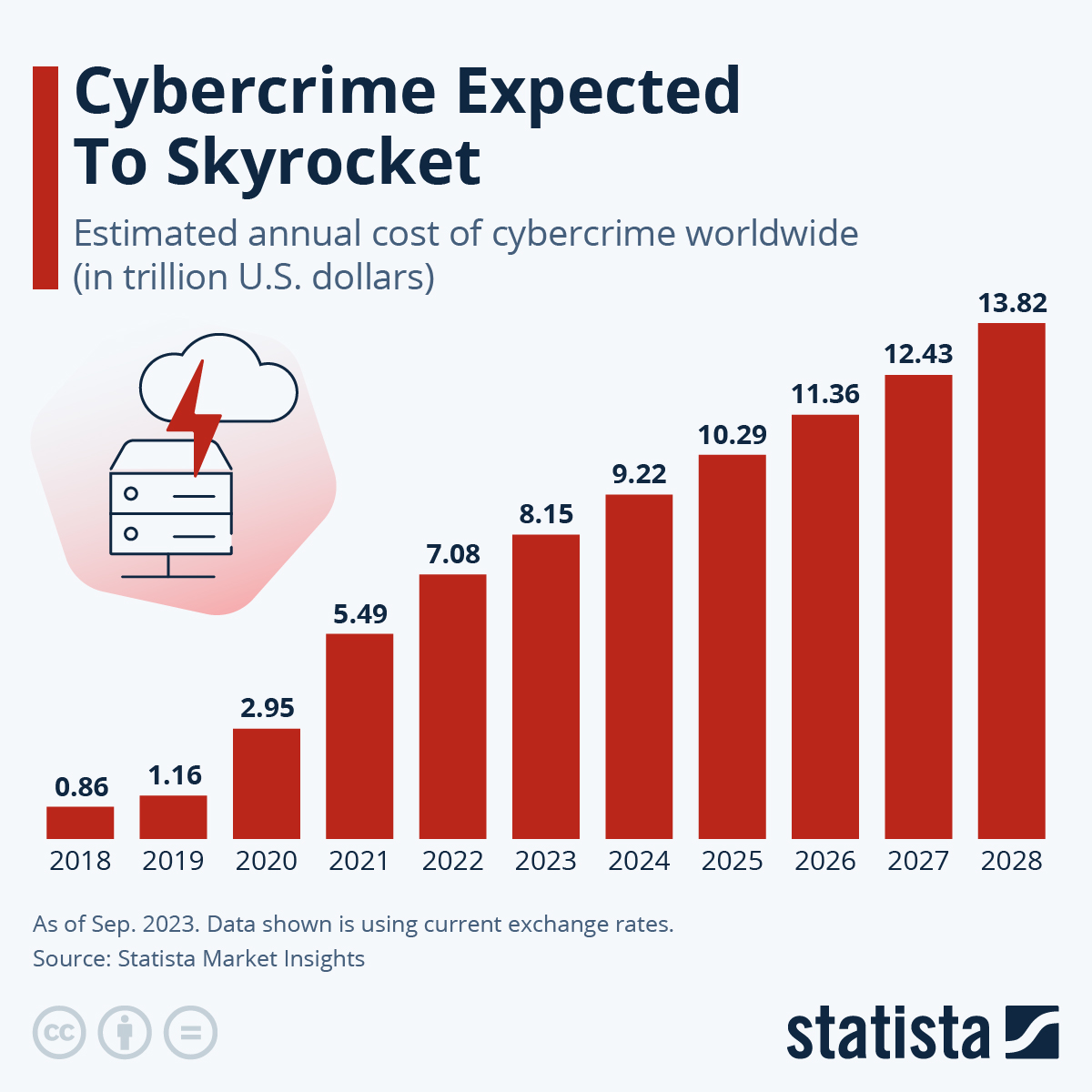
The Online Fraud and Scams in India report highlights how the threat landscape is shifting:
- AI & Generative AI misuse: Fraudsters are now using voice cloning, deepfake video, synthetic identities to execute frauds. These are harder to detect using traditional controls.
- Sectoral exposure: Fintech, e‐commerce, telecom are particularly affected. As digital payments, UPI usage, and online services proliferate, the attack surface grows.
- Cross‐border / Transnational fraud: Scam operations often originate outside India (e.g., Southeast Asia), complicating detection, regulation, prosecution.
- Regulatory gaps: Existing laws (like the IT Act 2000) do not specifically cover misuse of generative AI. While newer regulations like the DPDP Act 2023 focus on data protection, they are not fully tuned for AI‐fraud or cross-border scam operations.
As Gartner predicts that cyber attackers will weaponize operational technology environments by 2025, it is essential to take a proactive approach to security. By implementing a cybersecurity network architecture, organizations can potentially decrease the financial impact of security incidents by an estimated average of 90% by 2024.
Overview of VAPT and its Importance in Cybersecurity
VAPT, stands for Vulnerability Assessment and Penetration Testing, is a process of probing an organisation’s digital infrastructure (networks, applications, endpoints) for vulnerabilities, then simulating attacks to test how well the defenses hold up — is designed to find what might not be obvious, before attackers do. But how big is the dang
Moreover, it also involves staying up to date with the latest security trends, training employees on best practices for cybersecurity, and implementing policies and procedures to prevent and respond to cyberattacks. By understanding the importance of VAPT in the context of increasing technology complexity, organizations can take proactive measures to protect their digital assets and minimize the risk of cyber threats.
The market for security services is expected to grow $66.83 billion by 2030. This indicates that organizations are recognizing the value of protecting their digital assets and mitigating cyber risks. As organizations face increasing cyber threats, regulations, and compliance requirements, this trend is likely to persist. By investing in information security and risk management services, organizations can better protect themselves against cyberattacks, data breaches, and other security incidents, and minimize the potential impact on their operations, reputation, and financial health. Additionally, it is expected that increased expenditure will spur competition and innovation in the cybersecurity sector, resulting in the creation of more advanced and effective solutions that work.
Common Vulnerabilities and Their Consequences
VAPT can help identify various types of vulnerabilities in IT infrastructure. These vulnerabilities can range from software flaws to network configuration errors, and they can pose a significant threat to the security and stability of an organization's IT assets.
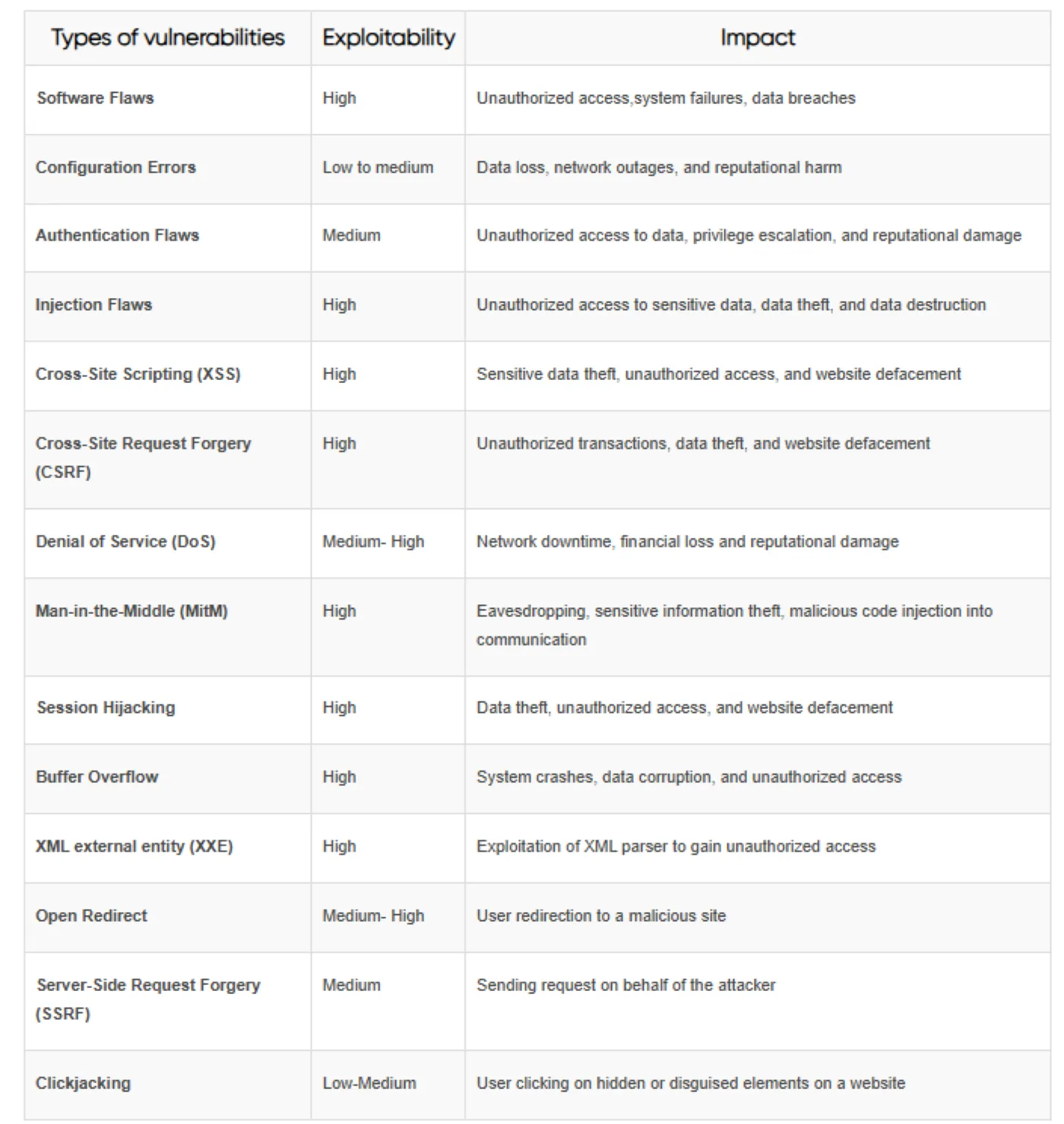
Note:
- Exploitability refers to the ease with which a vulnerability can be exploited by an attacker.
- Impact refers to the severity of the consequences if a vulnerability is exploited by an attacker.
From the table, it is evident that cyberattacks can cause financial loss, reputational damage, legal liabilities, and without VAPT services businesses are vulnerable to such attacks that can disrupt their operations and even force them to shut down.
In addition to the above, the surge in AI-driven fraud, phishing scams, and digital payment theft has exposed critical gaps in many organizations’ cybersecurity defenses. As fraudsters increasingly leverage deepfake videos, voice cloning, and synthetic identities, traditional security measures often fail to detect such sophisticated attacks. VAPT plays a crucial role here by simulating these emerging threat vectors to uncover weaknesses in identity verification systems, access controls, and authentication processes before they are exploited.
Similarly, with the sharp rise in UPI fraud and OTP-based scams, VAPT helps identify vulnerabilities within transaction workflows, user interface designs, and data validation mechanisms that could be manipulated by attackers. Beyond prevention, it also enables organizations to quantify their risk exposure and evaluate how effective their existing controls truly are.
How VAPT Should Be Integrated into a Cybersecurity Strategy
To respond to the threats above, VAPT should not be an afterthought but a core part of cybersecurity planning. Here are some recommended practices:
- Periodic VAPT cycles: Not once a year, but multiple times, especially when there are major changes (new services, new features, AI/ML usage, regulatory obligations).
- Simulated attack types aligned with current threat data: Include AI‐based phishing, impersonation, deepfake attempts, synthetic identity fraud in pen test scenarios.
- Holistic coverage: Network, application, infrastructure, identity management, and user behavior. Especially the endpoints and user authentication flows which fraudsters frequently exploit.
- Collaboration with law / compliance teams: Ensure that findings are not only remediated but also feed into risk assessments, compliance requirements (e.g. RBI guidelines, CERT-In advisories, PCI DSS, NIST, GDPR, SOC2, ISO 27001).
- Invest in detection & response: Even with VAPT, breaches might happen. Having good monitoring, incident response, threat intelligence, and forensic capability is essential.
Perhaps most importantly, VAPT gives leaders actionable insights into their overall security posture. For firms struggling with low confidence in their ability to detect and respond to modern cyber threats, VAPT provides empirical, evidence-based results that help them benchmark maturity levels, direct investments, and strengthen compliance readiness. By turning vulnerabilities into verified insights, VAPT empowers businesses to move from reactive firefighting to proactive risk management
Further Learning
Beyond Basic Cybersecurity: The Power of VAPT in Protecting Your Business
How Choosing the Right VAPT Service Provider Secures Your Digital Assets
Join our Community
Subscribe for exclusive updates and news.
Read about our privacy policy.



.svg)












.webp)
.webp)
.webp)
.webp)
.webp)
.svg)






.webp)

.webp)









































